Wordpress Local File Inclusion Vulnerability
WordPress Media Library Assistant 281 Local File Inclusion Posted Apr 13 2020 Authored by Daniel Monzon WordPress Media Library Assistant plugin version 281 suffers from a local file inclusion vulnerability. This parameter can be controlled by an attacker and is not properly sanitized.
 Comprehensive Guide On Remote File Inclusion Rfi
Comprehensive Guide On Remote File Inclusion Rfi
Remote and Local File Inclusion Vulnerabilities 101 And the Hackers Who Love Them 1.
Wordpress local file inclusion vulnerability. The attacker is able to access review download a local file on the server. Typically it is exploited by abusing Dynamic file inclusion mechanism that do not sanitize the user input. Local File Inclusion The File Inclusion vulnerability allows an attacker to include a file usually exploiting a dynamic file inclusion.
Webapps exploit for PHP platform. In this tutorial I show you how to get a shell on websites using Local File Inclusion LFI vulnerabilities and injection malicious code in procselfenvironIs a step by step tutorial. A Local File Inclusion vulnerability in the Nevma Adaptive Images plugin before 0667 for WordPress allows remote attackers to retrieve arbitrary files via the REQUESTadaptive-images-settingssource_file parameter in adaptive-images-scriptphp.
Depending upon the severity it can lead to Remote code execution XSS DOS sensitive. Executive Summary Remote and local file inclusion RFILFI attacks are a favorite choice for hackers and many security professionals arent noticing. This type of vulnerability is known as a Local File Inclusion LFIattack.
This attack chains together a Path Traversal and a Local File Inclusion LFI vulnerability in WordPress. Local File Inclusion LFI also known as path traversal vulnerability from which we can get the information of application code and data from web server credentials for back-end system and sensitive files like. Follow the following steps to hack website using LFI and upload shell on hacked website.
Mail Masta WP Local File Inclusion info. The attacker may do it by using or to reference a parent directory. Also read about a related vulnerability remote file inclusion RFI.
WordPress Plugin Media Library Assistant 281 - Local File Inclusion. LFI stands for Local File Inclusion which means that an attacker can target the files that are already present on the target web server. TimThumb a WordPress add-on.
By exploiting this vulnerability a remote unauthenticated attacker could retrieve arbitrary files from the target server. Local file inclusion LFI and directory traversal path traversal vulnerabilities let the attacker access the host system. 23-8-2016 Autor Guillermo Garcia Marcos Vendor.
Basically Local File Inclusion Vulnerability in wordpress is due to improper sanitization of ajax path parameter in requests to ajax shortcode pattern. Local File Inclusion LFI allows an attacker to include files on a server through the web browser. Local file inclusion LFI Fixed in version.
Local File Inclusion and Directory Traversal. The bugs were discovered in February 2019 by RipsTech and presented on their blog by Simon Scannell. In the case of directory traversal the attacker may read files that should not be accessible.
1 000 Local File Inclusion LFI vulnerability found by Erik David Martin in WordPress Backup by Supsystic plugin versions. A vulnerable CMS is an invitation for attacks which may lead to compromising the underlying server. This vulnerability exists when a web application includes a file without correctly sanitizing the.
No known fix plugin closed Number of sites affected. If an LFI vulnerability exists in a website or web application an attacker can include malicious files that are later run by this website or web application. Typically In most cases vulnerabilities in the web arise due to lack of adequate filters or improper input validation and the same thing that we have to face in this.
2021-02-08 we were unable to find a patched version of this plugin. This in case youre wondering is a very serious vulnerability that should have been addressed immediately. LFI is a web vulnerability caused by mistakes made by a programmer of a website or web application.
 What Is Local File Inclusion Vulnerability Quttera Web Security Blog
What Is Local File Inclusion Vulnerability Quttera Web Security Blog
File Path Traversal And File Inclusions Lfi Rfi By Asfiya Ha Kh Medium
 Wordpress Remote Local File Inclusion Vulnerability Exploit
Wordpress Remote Local File Inclusion Vulnerability Exploit
 From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
 From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
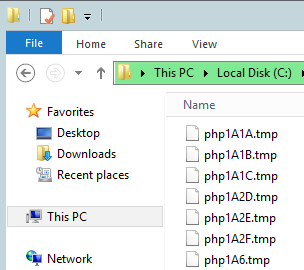
 Local File Inclusion With Tmp Files
Local File Inclusion With Tmp Files
 Wordpress Remote Local File Inclusion Vulnerability Exploit
Wordpress Remote Local File Inclusion Vulnerability Exploit
 From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
 Wordpress Remote Local File Inclusion Vulnerability Exploit
Wordpress Remote Local File Inclusion Vulnerability Exploit
 From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
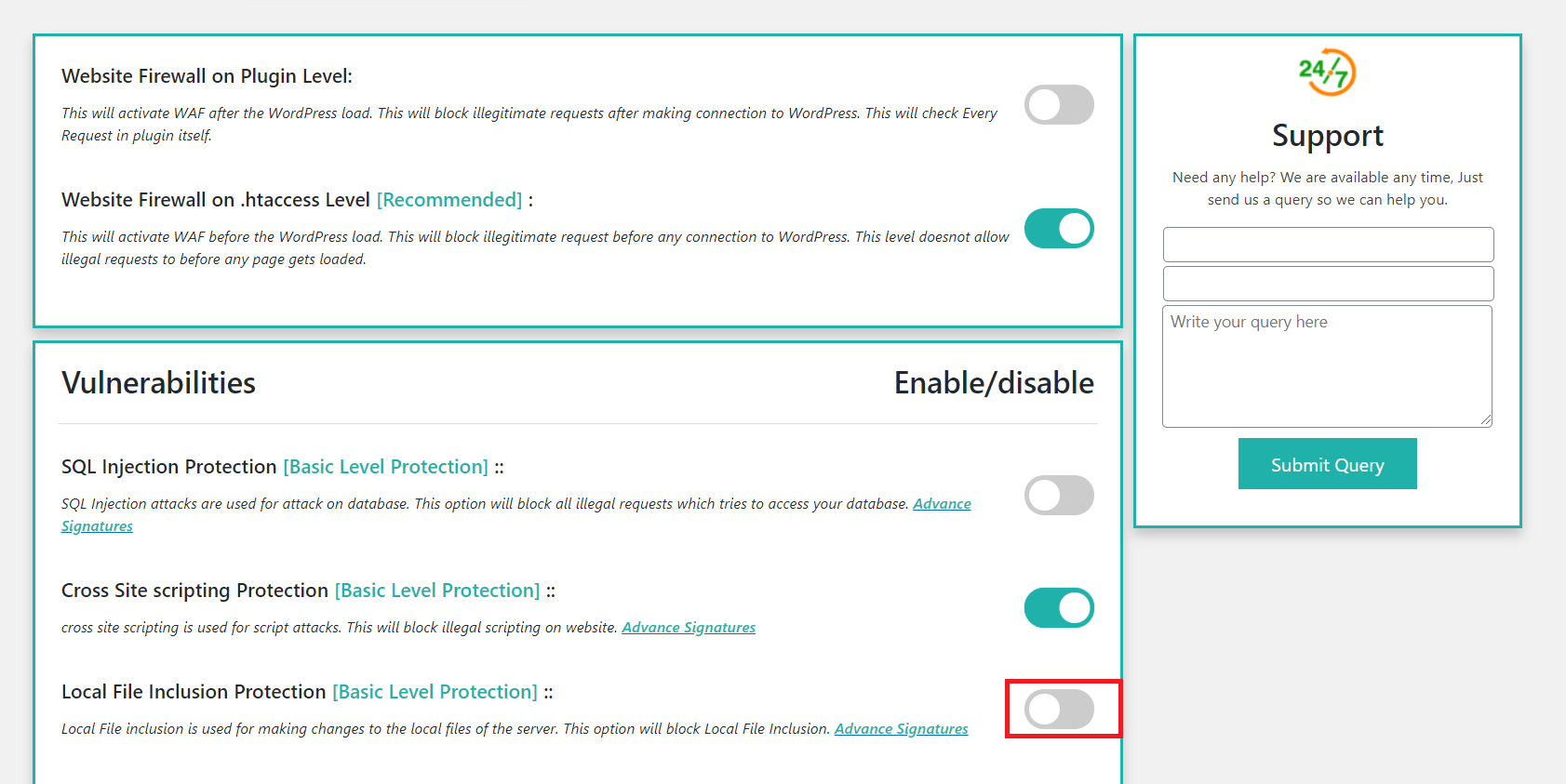 Wordpress Web Applicatoin Firewall Firewall
Wordpress Web Applicatoin Firewall Firewall
 The Remote File Inclusion Vulnerability Quttera Web Security Blog
The Remote File Inclusion Vulnerability Quttera Web Security Blog
 From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
From Local File Inclusion To Remote Code Execution Part 1 Outpost 24 Blog
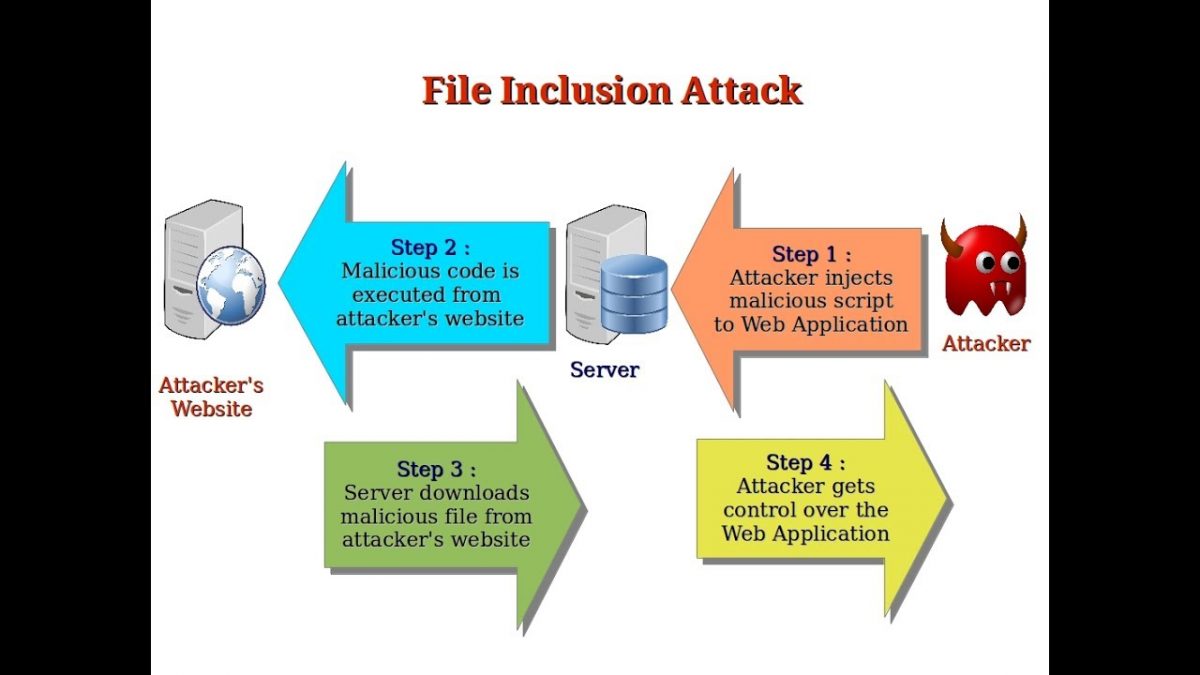 Remote File Inclusion Local File Inclusion I Iot Security News
Remote File Inclusion Local File Inclusion I Iot Security News
 Gilacms 1 11 8 Cm Delete T Lfi Local File Inclusion And Rce Infosecdb
Gilacms 1 11 8 Cm Delete T Lfi Local File Inclusion And Rce Infosecdb
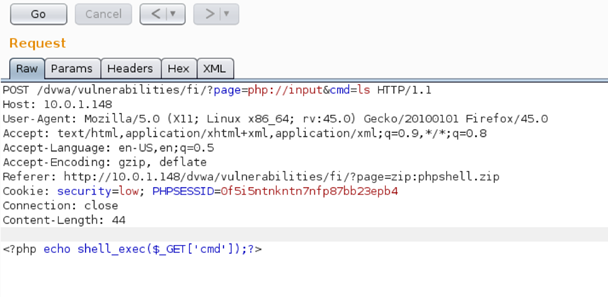 Wordpress Remote Local File Inclusion Vulnerability Exploit
Wordpress Remote Local File Inclusion Vulnerability Exploit
 Wordpress Remote Local File Inclusion Vulnerability Exploit
Wordpress Remote Local File Inclusion Vulnerability Exploit
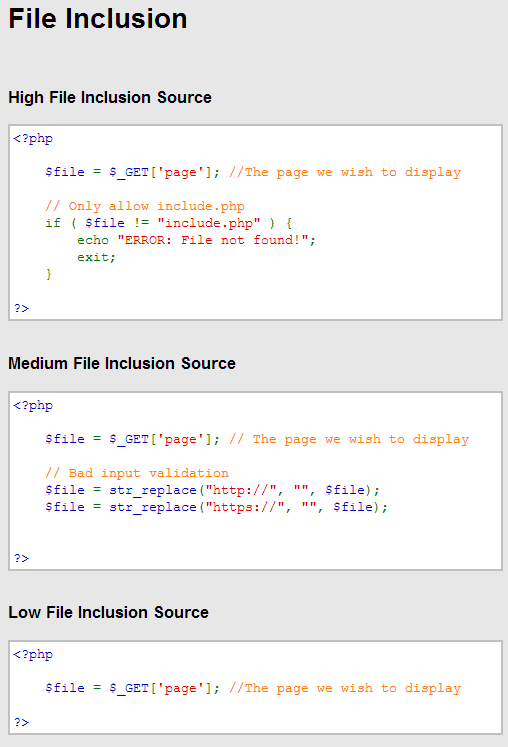 Local File Inclusion Remote Command Execution Ifconfig Dk
Local File Inclusion Remote Command Execution Ifconfig Dk
 Wordpress Remote Local File Inclusion Vulnerability Exploit
Wordpress Remote Local File Inclusion Vulnerability Exploit
Post a Comment for "Wordpress Local File Inclusion Vulnerability"